IM archiving and compliance tips for RIAs

Today’s RIAs are always on the go, so they rely more than ever on the convenience of chat apps to stay in touch with clients and colleagues. This is critical because sometimes responding in a timely manner spells the difference between investment success and failure. But with growing reliance on instant messaging (IM) comes a […]
Biometrics authentication for data security at your RIA

Data loss is a bigger concern than ever nowadays, as cyberattackers are getting creative with their breaches and exploits. So it’s a smart choice to add layers of security — such as biometrics authentication — to make your data as difficult as possible to steal. Authenticate your profile on your mobile device Chrome OS, Windows, […]
A Look at Microsoft Office Delve
Many small- and medium-sized RIAs have started using Microsoft 365 to enhance their processes and productivity. This means the amount of data created by Microsoft 365 is growing, posing some challenges in tracking connections and information. This is where the Office Delve feature comes in handy. What is Office Delve? Office Delve is a cloud-based […]
Should your RIA migrate away from Dropbox?

Dropbox is a popular file hosting service for personal users, but as with any freemium cloud service, it has also become a popular storage option for businesses. However, as threats of ransomware and other cyberattacks come to dominate the news, many Dropbox users have begun to wonder whether it’s truly a safe and reliable choice. […]
Microsoft Data Loss Prevention tools for RIAs

Microsoft provides a host of productivity and data management solutions for RIAs. So it comes as no surprise that the tech giant also offers ways to protect its enterprise users from data loss. Microsoft Data Loss Prevention (DLP) is one prime example. If you don’t know the term Data Loss Prevention – that’s ok. But […]
Microsoft Office 365 encryption for RIAs
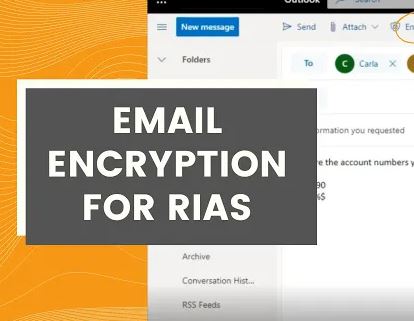
How to send an encrypted email. Opening an encrypted email.
If you’re using Microsoft Office and need to send confidential information via …
Know the risks from public charging kiosks

When your phone’s juice runs out and you’re nowhere near your charger, a public charging kiosk can look pretty promising. But what you might not know is that recharging phones at public charging stations can make you a victim of juice jacking. What is juice jacking? While newer phones can be charged wirelessly, older models […]
Two-step and two-factor authentication: What’s the difference?

Every RIA should have a strong cybersecurity posture to keep cybercriminals from infiltrating their network. One way to do this is by implementing a strict authentication process using two-step or two-factor authentication. These two processes are so similar that many confuse one with the other. Learn the difference between the two and how you can […]
How do Microsoft 365 Group connectors work?

The cross-application service in Microsoft 365 known as Groups enables members of a team to collaborate and share resources with one another. Those resources can be a calendar, spreadsheets, and even an Microsoft Outlook inbox, among others. Groups also has a feature called connectors that allows users to share content from third-party services right in […]